About WS-Security
In ReadyAPI, you can use WS-Security to make your requests safer.
For information about WS-Security, see http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=wss.
For information on how to create a keystore or truststore, see the documentation for the
keytoolcommand in Java: http://docs.oracle.com/javase/8/docs/technotes/tools/windows/keytool.html.For information about SAML, see http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=security.
Accessing the WS-Security Editor
To open WS-Security settings, switch to any node in the APIs section of the Navigator and select WSS Config from the Auth & Security drop-down on the toolbar.
 |
You can also select Project > WS-Security configurations from the main menu.
Important
In ReadyAPI 3.5.2 and earlier, you could set up WS-Security on the Endpoints page in the service editor. The page was reworked in 3.6.0 and no longer has this feature. If you update from 3.5.2 to a newer version, your WS-Security settings from the Endpoints page will be lost, and you will have to recreate them using the WS-Security Configuration dialog, as described below.
WS-Security Configuration Dialog
The WS-Security configuration dialog includes the following tabs:
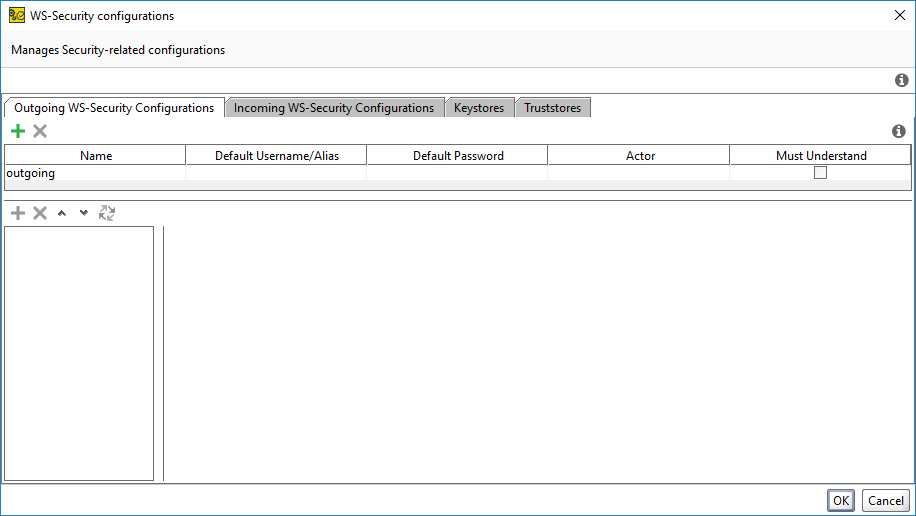 |
Outgoing WS-Security Configurations – Configurations that should be applied to outgoing messages, including requests and VirtResponses. This configuration type is used for encrypting, signing and adding SAML, and for timestamp and username headers.
Incoming WS-Security Configurations – Configurations that should be applied to incoming messages, including responses, VirtRequests, or monitored requests and responses. This configuration type is used for decrypting and verifying the signature of incoming messages.
Keystores – Keystores used for encryption, decryption, and signing.
Truststores – Truststores are used for signature verification.