SSL Client Auth
Planned Changes to Trust Manager in ReadyAPI 3.63.0 and 3.64.0
We plan to release improvements to the Trust Manager in ReadyAPI 3.63.0 and 3.64.0. These updates introduce more granular controls for handling self-signed certificates.
ReadyAPI will require you to specify and whitelist trusted certificates. This reduces the risk of man-in-the-middle attacks and preserves Transport Layer Security (TLS) protections.
Starting in ReadyAPI 3.63.0, a new interface lets you view, add, and whitelist SSL certificates. Certificates that previously triggered errors also appear in this view.
 |
These changes redefine how ReadyAPI manages trust and SSL certificates. Currently, ReadyAPI does not validate certificates for HTTPS calls. Starting from ReadyAPI 3.63.0, you can configure ReadyAPI to detect untrusted certificates and enforce whitelisting for certificates that previously encountered errors.
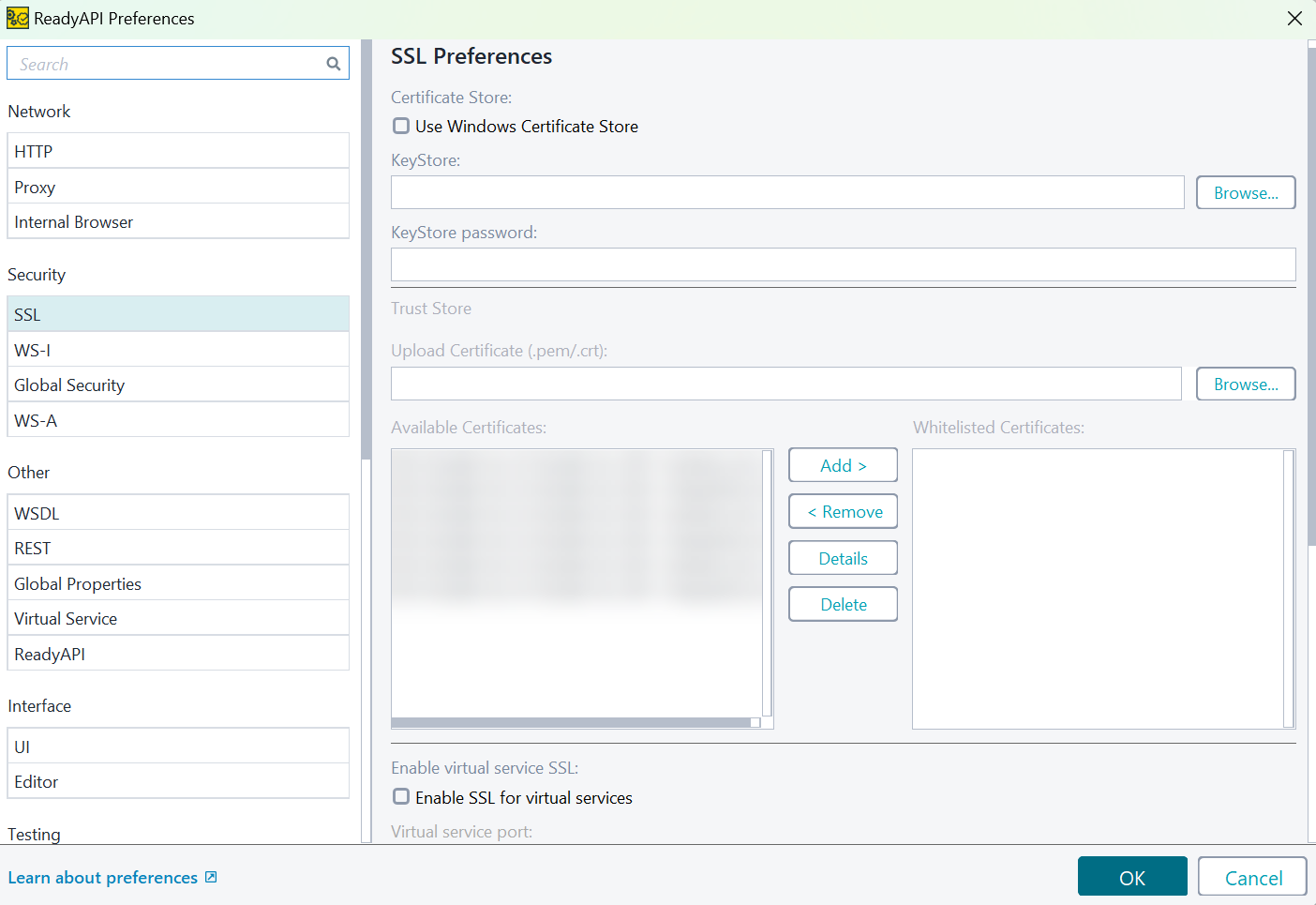
A new Trust Store section under SSL in Global Preferences will display a list of untrusted certificates that ReadyAPI encountered. When you select any certificate, the certificate details will display in a pop-up window.
Selecting one or more certificates and choosing Whitelist adds them to .cacerts in the .readyapi directory. Uploading a certificate file directly also adds it to .cacerts in the .readyapi directory.
On startup, ReadyAPI checks for .cacerts in the .readyapi folder. If no file exists, ReadyAPI creates a copy from the bundled Java .cacerts. A unified mechanism now links the Trust Manager to the .cacerts file in .readyapi.
This feature will be available but off by default in ReadyAPI 3.63.0 and enabled by default in ReadyAPI 3.64.0. This notice provides time to test the feature in 3.63.0 and prepare for its default activation in ReadyAPI 3.64.0.
ReadyAPI can use SSL client certificates to secure your connection to the server.
About client certificate authentication
When setting up an HTTPS connection, your client requests a certificate from the server to establish the server's identity. This creates a secure connection, but the server does not know who the client is. To make sure the client who can access the secure server is qualified, you use client certificate authentication.
When you use client authentication, the client sends its SSL certificate after it verifies the server identity. Then, the client and server use both certificates to generate a unique key used to sign requests sent between them.
ReadyAPI can use your certificates to secure the interactions with the server.
Requirements
ReadyAPI supports JKS (
.jks), JCEKS (.jceks), and PKCS12 (.p12,.pfx) keystores.The certificate file you use must contain the entire certificate chain, including the root certificate. Otherwise, the server may fail to verify the client identity.
Use a valid certificate that a server can trust. The certificate must have a digital signature from the authority trusted by the server, a valid expiration date, and should not be revoked.
Using client certificates
For all requests
Open the ReadyAPI Preferences dialog:
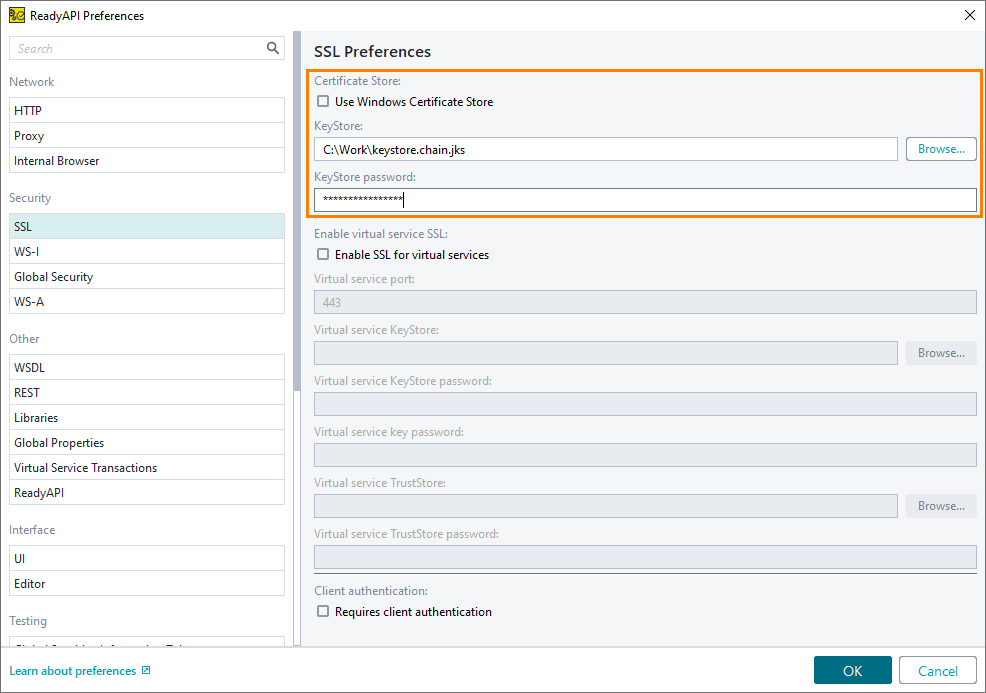
Switch to the SSL page. On this page, specify the KeyStore that contains the client certificate and the KeyStore password.
If you use Windows, you can also use certificates located in the Windows Personal Certificate Store. For this, enable the Certificate Store option.
For a specific request
Select an element in the APIs node in the Navigator panel and click Auth & Security > WSS Config on the toolbar:
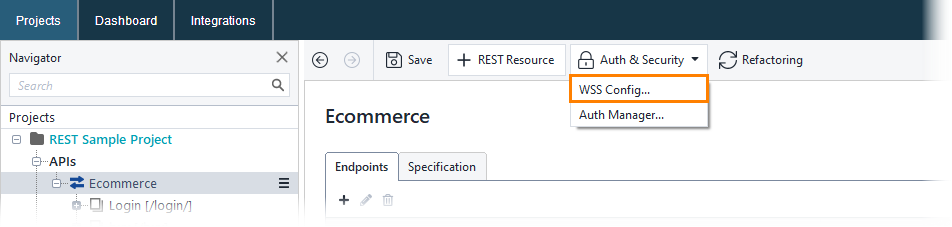
This will open the WS-Security configuration dialog.
In the dialog, switch to the Keystores tab and click
 :
: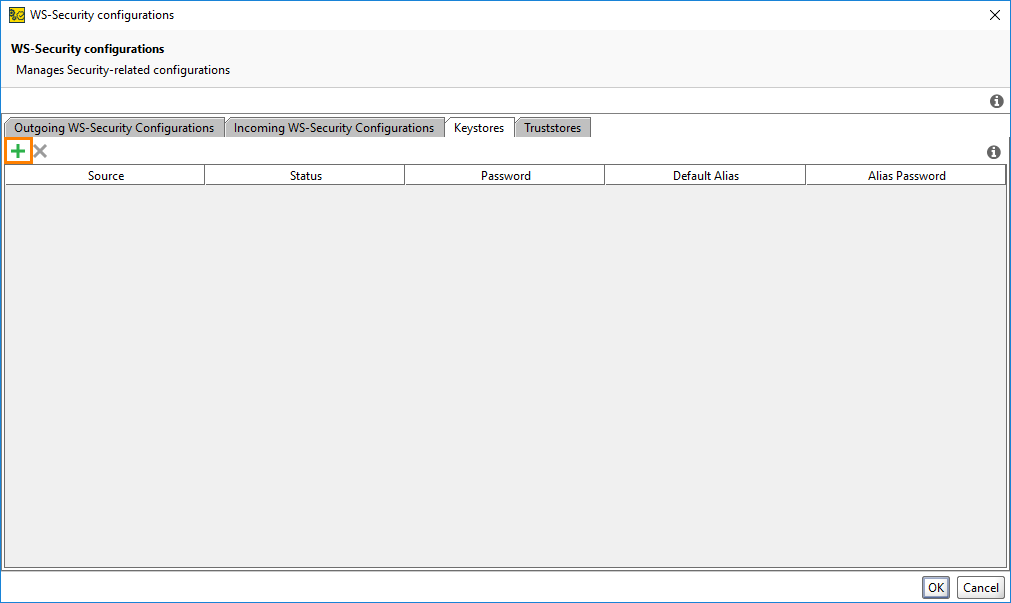
Select the keystore file and specify the password. If the keystore is imported successfully, the Status column will display OK:
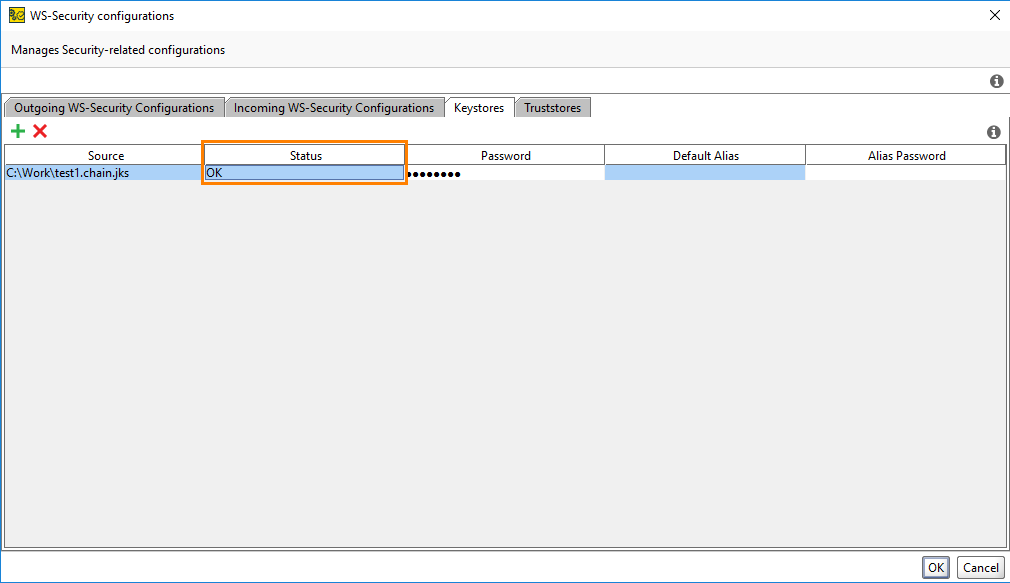
Close the WS-Security Configuration dialog.
Select the request you want to apply the certificate to (you can select the request in the Navigator panel in Projects or select the request test step in ReadyAPI Test). Use the drop-down list in the SSL Keystore property to select the keystore:
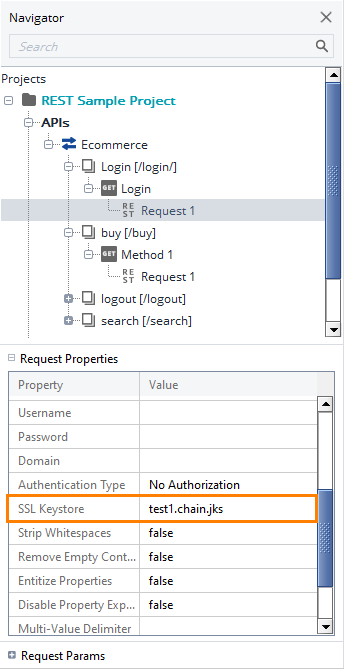
Tip
Request properties depend on the environment you use. When working with multiple servers that require different certificates, set up environments to quickly switch the certificate used.