Deploy SwaggerHub On-Premise from AWS EC2 Console
Follow these steps to launch a SwaggerHub On-Premise instance from the AWS EC2 console. The console allows you to fine-tune the configuration before launching the instance. Existing Users of SwaggerHub On-Premise 1.x in AWS who need to deploy via the EC2 console must file a support ticket with Customer Service for help.
Note
Another way is to launch a SwaggerHub On-Premise instance from the AWS Marketplace. This can be done to quickly launch an instance with the recommended default options.
Prerequisites
Before deploying SwaggerHub On-Premise on AWS, you must have the following:
An AWS account. You can sign up at https://aws.amazon.com.
The SwaggerHub On-Premise 1.x license file that was provided by a SmartBear representative when you set up your account.
An AWS private image provided by SmartBear Customer Service
1. Set up a Virtual Private Cloud (VPC)
A VPC is an isolated network within an Amazon region where you can deploy EC2 instances and host other resources. You have complete control over the VPC configuration, including the IP range, subnets, routing tables, network gateways, and security.
All new AWS accounts include a default VPC in each AWS region. The default VPC comes with a public subnet, meaning that EC2 instances from that subnet will have direct Internet access. VPCs can also have private subnets where instances can connect only to the Internet via NAT and cannot be accessed directly from outside the VPC.
If you don’t have a VPC in your preferred AWS region, or if you need a specific VPC configuration, you can create your own VPC and configure it as required. To learn how to create VPCs, see Creating a VPC and Scenarios and Examples in the AWS documentation.
2. Launch a SwaggerHub On-Premise instance
SmartBear Customer Support will guide you through this process.
3. Set up the instance
Select an instance type for SwaggerHub On-Premise. The instance type specifies the hardware configuration for your EC2 instance. We recommend r5.large or a similar instance type that meets the minimum system requirements:
Memory: 15.25 GB or more
CPU: 2 virtual cores
Storage: EBS only
To learn more about instance types and their pricing, see AWS Instance Types and Amazon EC2 Pricing.
On the Configure Instance Details screen, specify the following:
Option
Value
Number of Instances
1
Purchasing option
Leave unselected
Network and Subnet
Select the VPC and subnet where you want to launch SwaggerHub On-Premise
Auto-assign Public IP
Use subnet settings
Placement group
Leave unselected
Capacity Reservation
Select what you need
IAM role
Optional – select if required
CPU options
Optional – change if required, but make sure that Number of vCPUs is at least 2
Shutdown behavior
Stop
Stop - Hibernate behavior
Optional – select if required
Enable termination protection
Optional – select if required
Monitoring
Optional – select if required
Tenancy
Select what you need
File systems
Leave as is
For more information about these options, see the AWS documentation.
Click Next: Add Storage.
Leave the default storage (200 GB, root volume).
Click Next: Add Tags.
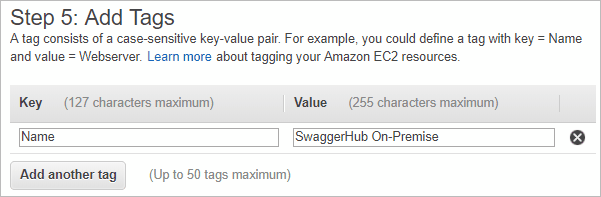
Add a tag with key = Name and value = SwaggerHub On-Premise. The instance name can be used to identify it in the AWS console.
Add other tags, if required.
Click Next: Configure Security Group.
Select an option to Create a new security group, change the Security group name to SwaggerHub On-Premise, and specify the following rules:
Type
Protocol
Port Range
Source
Description
SSH
TCP
22
Anywhere
SSH access to SwaggerHub
HTTP
TCP
80
Anywhere
HTTPS
TCP
443
Anywhere
Optional – needed only if you are going to install an SSL certificate directly to the SwaggerHub On-Premise instance. If you are going to offload SSL to a load balancer, this rule is not needed.
Custom ICMP
Echo Request
N/A
Anywhere
Optional – use it if you want to be able to ping the instance by its IP
Note
Anywhere or 0.0.0.0/0, ::/0 allows inbound access from all IP addresses. It can be used temporarily for testing purposes. In production, you will want to authorize a specific IP range instead.
Click Review and Launch.
Review the configuration and click Launch.
You will be prompted to select an existing key pair or create a new key pair. A key pair is used to access the instance using SSH. You can also proceed without a key pair and add SSH keys later through the SwaggerHub Admin Center.
Select the desired option, then select the acknowledgment check box and click Launch.
Wait for the instance to come up.
Note
Launching the instance for the first time may take several minutes.
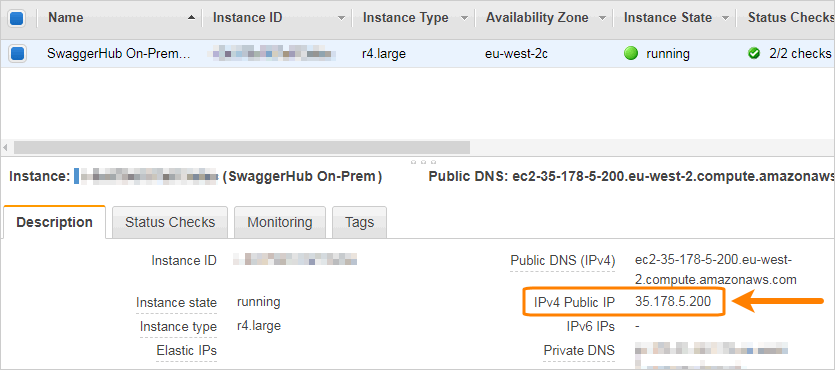
After the instance is up again, note down its IP address:
4. Initial SwaggerHub configuration
Navigate to
http://IP_address/uito access the installer.Configure basic system settings, including the admin username and password. Important: Enter the instance’s IP address in the DNS name for this instance field.
Log in to the SwaggerHub Admin Center using the created admin user. Here you can configure additional system settings.
After the setup, you can access the SwaggerHub application at http://IP_address, and the SwaggerHub Admin Center at http://IP_address/ui.
You can also connect to the instance via SSH using its IP address, the username ubuntu, and the private key from the key pair you selected when launching the instance.
5. Monitor instance health
AWS provides status checks to monitor the operational status of EC2 instances. You can configure status check alarms to get notified when an issue is detected.
In the EC2 Console, go to Instances.
Select your SwaggerHub On-Premise instance and switch to the Status Checks tab at the bottom.
Click Create Status Check Alarm.
Specify the following options:
Send a notification to – the user to send a notification to
Whenever – Status Check Failed (Any)
Name of alarm – enter a unique name for this alarm
Leave the default values for the other options.
Click Create Alarm.
In addition to status checks, you can configure CloudWatch alarms to monitor the CPU usage and other metrics and get alerted when these metrics reach critical levels. To learn more about using CloudWatch, refer to the CloudWatch documentation.