LDAP
Settings on the LDAP tab (pictured below) specify the LDAP provider to which the On-Premise License Server connects to get information on user accounts. By configuring LDAP:
License administrators can assign license seats to users by users’ distinguished names ("User DN").
License users enter their User DN and password to take up a license seat.
Your teammates can log in to the Licensing Portal by using their User DNs and passwords.
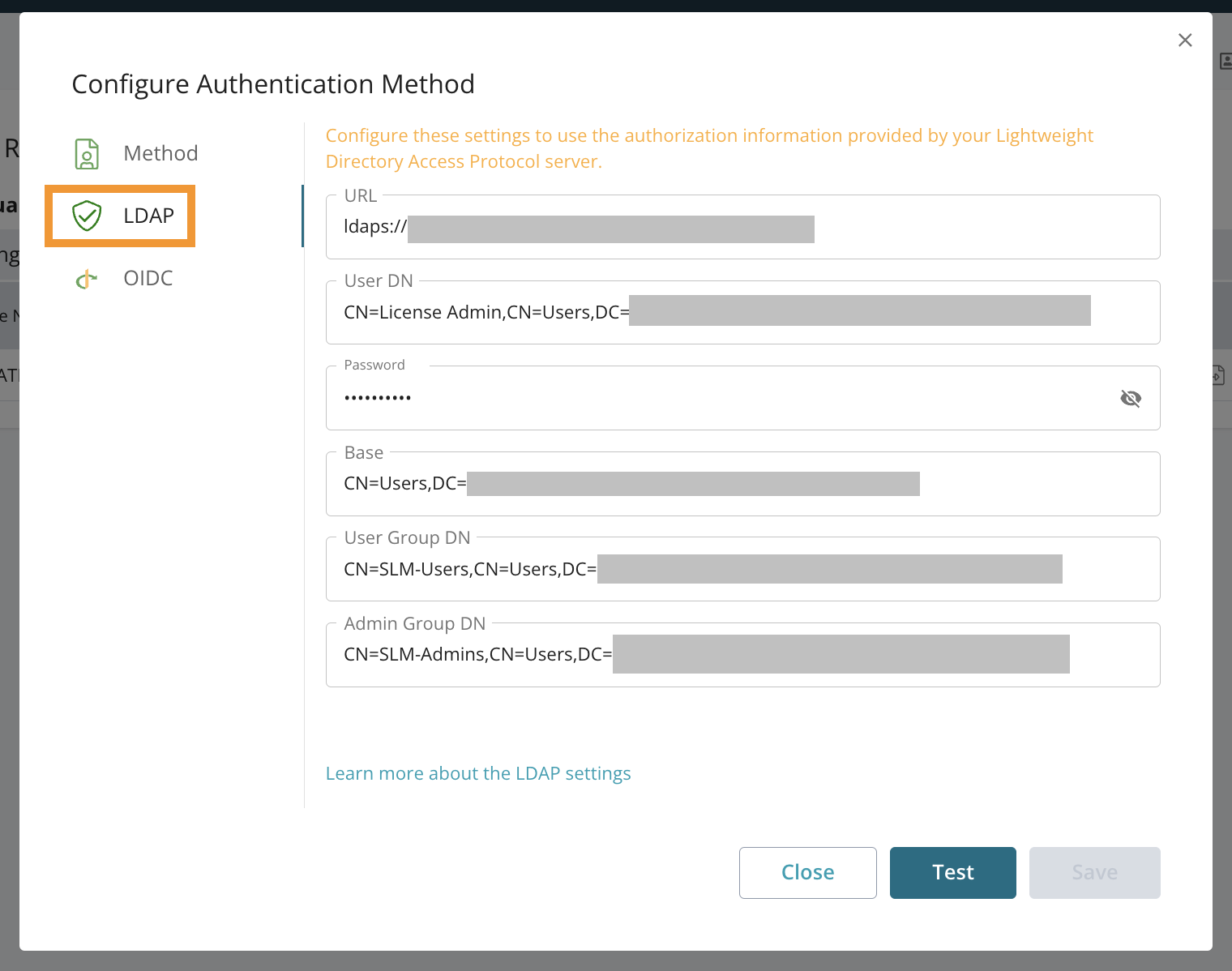 |
Your network administrator can help you specify the values requested in these fields. Here are definitions for them:
Field | Definition |
|---|---|
URL | LDAP server URL |
User DN | User Distinguished Name: The user account used for the "Bind and Search" operation against your LDAP domain – often the login email address |
Password | The password for the User DN LDAP Account – often the login password |
Base | The LDAP Search Base for all License Management users. Any user attempting to log in must be inside the base search. |
User Group DN | User Group Distinguished Name: The Fully Qualified Distinguished Name (FQDN) of an LDAP security group. Users must be members of this group to log in to an ID-based SmartBear product. |
The License Server implements standard LDAP algorithms and should be able to work with any Windows and Linux LDAP providers.
Click Test to check the connection to your LDAP provider. If the connection fails, double-check the settings and check again. Save the changes when you are done.
Configure LDAPS
LDAPS is configured by adding the CA certificate to the application's trusted store. Find out about requesting a CA certificate, see Configure for HTTPS and then perform the following steps:
Locate file
slm_service.vmoptionsin the License Management installation folder:Windows:
C:\Program Files\SmartBear\LicenseManager\binLinux:
/opt/SmartBear/LicenseManager/bin
Open it in a text editor and add the following parameters:
1. -Djavax.net.ssl.trustStoreType=PKCS12 2. -Djavax.net.ssl.trustStore=ca_certificate_file.p12 3. -Djavax.net.ssl.trustStorePassword=<password>