Account Setup
Learn how to configure your Reflect account.
Invite Users
To add additional users to your Reflect account, navigate to the User Management section under Settings and click the Invite User button. Within the Invite User modal, enter the invitee’s name and email address, and select the role that should be associated with the new user.
After clicking Send Invite, this user will be added to your Reflect account, and an automated email will be sent to the invitee with instructions on how to sign in.
User Permissions
Each user of a Reflect account is assigned one of the following permissions: read-only, editor, manager or administrator.
Read-Only
Read-only users can view test results and receive email notifications, but cannot create, edit or delete tests. Read-only users allow you to give access to people in your organization who should be informed of test results, but otherwise aren’t creating or maintaining tests.
Editor
Editors can perform most day-to-day tasks in Reflect. This role should be given to those creating and running tests and suites. Editors can also create and modify variables.
Manager
In addition to having all of the permissions of an Editor, a Manager can also modify the account’s integrations, as well as manage the non-Administrator users of the account.
Administrator
Along with everything Managers can do, Adminstrators can manage the account’s subscription plan, view the invoice history, and edit the current payment method. Finally, Adminstrators can also manage other Adminstrator users.
Single-Sign On
Your Reflect account can be configured to enforce all users to log in via a Single Sign-On (SSO) provider.
Within the User Management page, the Security section displays the options available for configuring single-sign on enforcement:
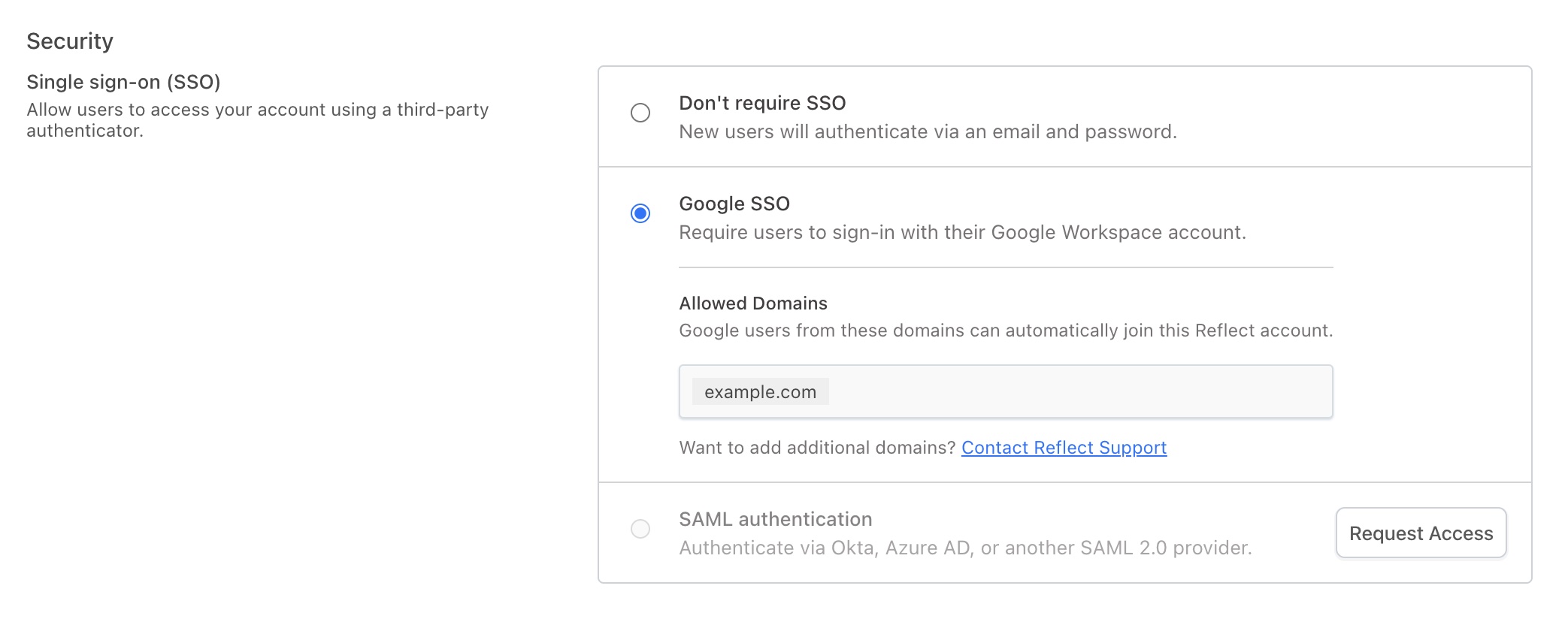
Don’t require SSO - This setting does not enforce any SSO policies, and it is the default setting for all Reflect accounts. When this setting is enabled, invited users join the account using their email address and a password.
Google SSO - When this setting is enabled, users who (1) sign in using their Google Workspace credentials and (2) are signing in with a domain that matches one of the domains listed in the Allowed Domains list, will be able to automatically join this Reflect account. Note that enabling this policy will not modify any existing users who are configured to sign in with an email address and password. To enforce this policy for existing users, delete the non-compliant users within the Users section and ask them to sign in and rejoin the Reflect account using their Google credentials.
SAML authentication - When this setting is enabled, access and authentication is handled by your SAML 2.0 compatible identity provider, such as Okta, Azure Active Directory, or PingOne. This option in only available to Enterprise customers.
Subscription Plan
You can view or modify your existing subscription plan at any time by visiting the Billing & Subscription page. From there, you can upgrade, downgrade, or move to a Read-only “Free” tier.