About
The AlertSite security monitor (device) identifies vulnerabilities, categorizes risks and gives recommendations on keeping your website safe from hackers. The monitor works with websites, servers, routers, firewalls and Internet-connected devices. It checks whether your website passes the “SANS Top 20 Internet Security Vulnerabilities” checklist as it is defined by SANS, the FBI and Federal Computer Incident Response Center (FedCIRC).
Currently, you can create and run security monitors in AlertSite 1.0.
Why Use the Security Monitor?
-
It helps you easily check if your website or service is attackable, with no need to install and configure additional software for this.
-
It examines all Internet-connected devices, ports, routers and firewalls from outside your network.
-
It provides thorough reports on detected services, open IP ports and vulnerabilities.
-
It automatically compares scan results with previous results and immediately sends a notification when a new issue is detected.
-
In case of false-positives, you can easily exclude them from future scans.
Create the Monitor
1. Purchase a Security Plan
Before creating security scans, you need to purchase a security plan. Please contact your account manager for details. You can find the contact information in AlertSite 1.0, under Account > Purchase Credits.
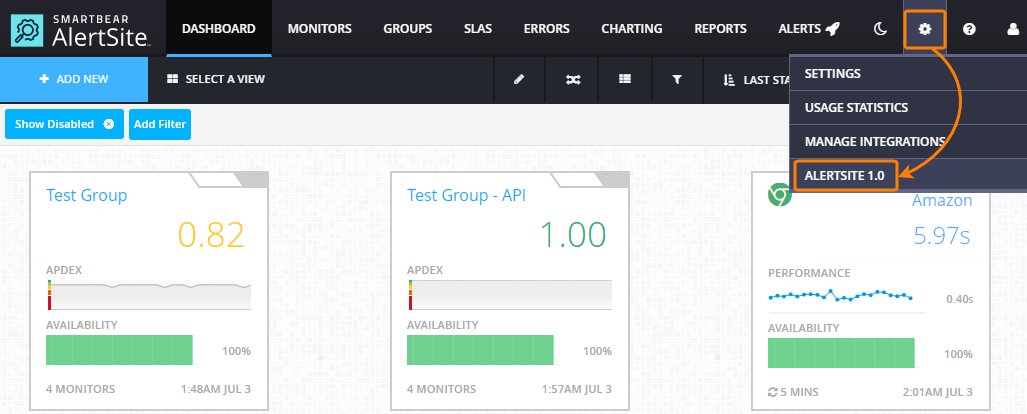
2. Switch to AlertSite 1.0
You create and run security monitors in AlertSite 1.0. To switch from AlertSite UXM to AlertSite 1.0, select > AlertSite 1.0 from the top menu:
3. Configure Monitor Settings
-
In AlertSite 1.0, select Configuration > Security Devices from the main menu.
-
Click Add a New Device in the top right corner.
If you do not have a security scan plan, you will be prompted to purchase it (see above). Otherwise, you will have to specify new monitor properties.
-
Set the properties of the new monitor. Click Submit in the top right corner to save the changes.
Monitor Settings
Device Name
The monitor name as it will be displayed in the AlertSite UI and reports.
Site Plan
Either Vulnerability Scan - weekly, or Vulnerability Scan - daily, depending on what you purchased. Select a value from the drop-down list.
Hostname
The name of the computer being scanned.
Notes:
-
Adding a security monitor by using the host name immediately resolves the host name to its IP address. The host name is also resolved every time the monitor runs. If the IP address changes, the Hostname property will reflect this.
-
Host names with multiple IP addresses (IP aliases) are currently not supported.
IP Address
The IP address (IPv4) of the scanned website, service or device connected to the Internet.
Scanning is
The monitor status. Default: Disabled. Select Enabled to activate the monitor.
Frequency
How often the monitor will run. Select either Daily, Weekly, or Monthly. The run period must be equal to or greater than the plan you purchased.
Notify?
If Yes (default), the monitor will send a notification if the scan results differ from the previous results, for example, if a new vulnerability is detected.
Day of scan (if weekly)
Select a day of the week for the scan, if you have a weekly scan plan.
Scan hour
Select the time the scan will begin.
Scanners
The security monitor can scan your website from different locations worldwide. The IP addresses of the scanners and their network providers can change. For the actual information on the scanners used, open the Monitoring Locations page and scroll it down to the SECURITY SCANNERS LOCATIONS section.
 Make sure your proxies or firewalls allow incoming requests from these IP addresses.
Make sure your proxies or firewalls allow incoming requests from these IP addresses.
Run the Scan
You can schedule scans when creating the monitor, or run a scan on demand.
How It Works
The security monitor is a network scanner based on the Nessus model, it is not an application scanner. It scans ports. If a port responds, the monitor checks it for possible vulnerabilities even if no program is actually running on that port.
Safety Settings
AlertSite uses the Nessus Safe Checks setting, so scanning is non-invasive and non-intrusive. The monitor tries to detect dangerous conditions without actually exploiting them. The setting disables many dangerous operations which may affect the availability or stability of the checked website or resource. Also, it prevents sending POST requests to remote CGIs in an attempt to identify SQL injections.
Initial Probe (Dead Host Check)
The scan begins with an attempt to establish a TCP connection to the following ports (in the order specified below) on the tested website or resource:
22 80 139 443 445 21 23 25 53 79 110 113 135 143 264 389
993 1454 1723 3389 8080 1521 111 5432 1433 44444
If none of these ports responds (full TCP handshake), the monitor considers the host dead and does not perform further tests.
Port Coverage (Ports Scanned by Standard Scans)
The next scan checks the ports defined by IANA. All publicly available services will appear in this list. The list is updated frequently and can be found in the IANA Port Numbers List.
Website Spidering
The monitor will spider up to 200 pages found on the website through the default document. Spidering helps you locate and identify popular CGIs to test.
Notifications on Issues
After the scanning is over, the monitor generates a scan report and compares it with the previous report it has. If it detects new vulnerabilities, it sends alerts and email notifications to you.
Security Reports
The security monitor creates the following types of reports. To view them, select Reports > Document Manager from the main menu:
| Report Type | Description |
|---|---|
| Demand Security Report | A detailed report that AlertSite creates after an on-demand (user-initiated) scan completes. |
| Security Scan Summary | A brief report listing only the changes in the security status of the checked website or device. Appears only when the monitor detects changes in the results relative to the previous results (for example, if a new vulnerability is found). |
| Automated Detail Report | A detailed report, identical to the Demand Security Report, created when the monitor detects a new vulnerability or issue. |
| A report that is automatically generated weekly or daily for weekly and daily monitors. AlertSite generates these reports early in the morning (about 6:00 AM EST). |
The reports contain the following sections:
| Report Section | Description |
|---|---|
| Synopsis | A brief description of the found vulnerability. |
| Description | A detailed description of the found vulnerability and an explanation why it was flagged. |
| See also | The websites that contain information to assist you in your investigation. |
| Risk factor | An estimated risk rating based on the vulnerability type. |
| Plugin output | The output of the Nessus scan. |
If you are sure there is nothing that makes the port vulnerable, mark it as a false positive (see below).
If the scan returns no results, you may need to configure your proxy or firewall to allow incoming messages from our security scanners’ IP addresses. Please see the AlertSite Monitoring Locations table. Scroll down to the section titled SECURITY SCANNERS LOCATIONS to get the latest IP addresses for the security scan servers.
Notes:
-
Generating a security report can take up to 2 hours.
-
For security reasons, these reports cannot be sent via email.
False Positives
False positives occur when the remote server does not return HTTP code 404 for invalid (file-not-found) requests, but instead, it returns a custom error page with a 200 OK reply. This makes Nessus consider the tested page existing, and triggers a vulnerability. You can mark the current results as false-positive by selecting their check boxes in the report. To prevent future false-positives, configure your web server to return the HTTP 404 response code along with your custom 404 page.
Get Security Seal
You can add an AlertSite security seal to your website to assure your customers that their sensitive information is protected. A security seal is an HTML code that include an image URL wrapped with a link, something like:
<img src="http://www.alertsite.com/security_seal/get/HOST-NAME-HERE/1.png">
</a>
To add a security seal to your website:
-
From the main menu, select Account > Create a Site Seal.
-
Follow the instructions on the subsequent page to get the HTML code of the seal.
You can add the seal HTML code to any page of your website.
Note that the security seal image appears if –
-
The monitor status is green (no vulnerabilities, or all the issues are set as false-positive), and
-
The Hostname property exactly matches the host name in the HTML code of the seal.