About
The Cross Site Scripting (XSS) scan checks how your service handles potentially harmful injections into web pages.
Typically, an attacker uses scripts targeting service users instead of the service itself. For example, if you have a comment form, an attacker sends the following commentContent:
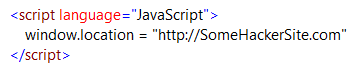
If approved, this script forwards users to a different website. Other harmful scripts record keyboard inputs and send them to the third-party server. The Cross Site Scripting scan simulates malicious scripts, enabling you to prepare a workaround for such issues.
If the scan does not reveal any information about possible vulnerabilities, it passes successfully.
If the scan has Failed, that may indicate your service is vulnerable to scripts sent from the browser side.
Requirements
This scan is applicable to all types of test steps or requests.
How it works
The Cross Site Scripting scan tries to attack the web service by replacing the original parameters of a test step with harmless strings, which resemble the malicious strings that are used in real attacks. It injects these strings to both XML elements and JSON fields.
This scan uses assertions to validate requests and responses and check if they include any information about potential vulnerabilities.
If all assertions pass successfully, PASS will be logged for that response. If any assertion fails, FAIL will be logged.
 |
If you have not applied any assertions to the scan, Unknown will be logged for the response. |
Assertions
-
Default Assertions
Cross Site Scripting – Verifies a response for injection strings and other content which reveals system information.
Sensitive Information Exposure – Verifies that your server does not reveal any information that is useful for attacks (such as stack traces if the server crashes).
Parameters
The Cross Site Scripting scan works by inserting values into the message parameters.
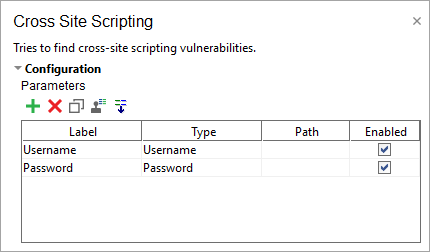
Normally, parameters are extracted automatically when you create the scan. See Parameters for more information.
Use the following options to configure the scan Strategy:
| Option | Description |
|---|---|
| Select Strategy |
One by One – Select to iteratively test each string for each selected parameter, leaving all parameters but the currently tested ones with their original value.
All At Once – Select to iterate through the list of strings just once, applying the same string to all the selected parameters. |
| Request Delay (ms) | Set a pause between requests during the scan in milliseconds. |
| Apply to Failed Test Steps | Select to run the scan even if the target test step fails. |
| Run only once | Select to run the scan only once for each test step, even if ReadyAPI runs that step several times for a test case. |
The Advanced panel contains a list of strings used by the cross-site scripting security scan to modify the parameters.
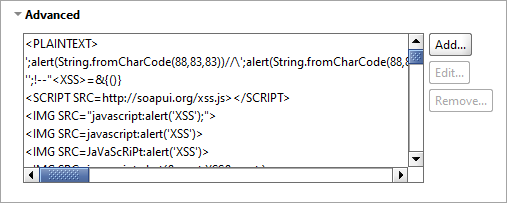
Add, remove, or modify the XSS lines in the list as needed.
