About
The Malicious Attachment scan generates corrupted files to check how your service behaves when receiving malicious files.
Typically, attackers will attach malicious files to a request for one of these purposes:
-
Trying to cause the server to crash with corrupted or very large files.
-
Damaging servers with viruses or files containing harmful code.
-
Passing viruses or files containing harmful code through the server, when the attack target is a client.
The Malicious Attachment scan provides a convenient way to ensure that your server handles malicious files safely.
If the scan does not reveal any information about possible vulnerabilities, it passes successfully.
If the scan has Failed, that may indicate your service cannot handle malicious files efficiently, which may cause security problems.
Requirements
This scan is applicable to SOAP test steps or requests that have file attachments.
How it works
The Malicious Attachments scan adds or replaces already existing attachments of the request. It tries to send invalid or large attachments to the server in order to provoke errors and compromise the security.
This scan uses assertions to validate each response and check if it includes any information about potential vulnerabilities.
If a response passes all assertions, PASS will be logged for that response. If any assertion fails, FAIL will be logged.
 |
If you have not applied any assertions to the scan, Unknown will be logged for the response. |
Assertions
-
Default Assertion
Sensitive Information Exposure – Verifies that your server does not reveal any information that is useful for attacks (such as stack traces, if the server crashes). -
Recommended Assertion
Response SLA – Verifies that your service responds within expected time even after receiving unexpected input.
Parameters
To configure the Malicious Attachment scan, click Open Editor in the Malicious Attachment scan inspector.
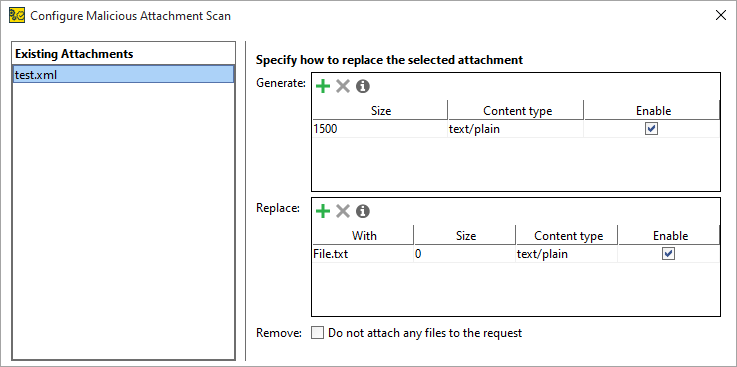
The Configure Malicious Attachment Scan dialog appears.
In the dialog, define the parameters of the Malicious Attachment scan:
-
The Existing Attachments table lists the attachments already added to the request. When you select one of these attachments, use the Generate and Replace tables to define how the attachment should be handled in the scan.
-
The Generate table allows you to create attachments. These attachments are not stored on the disk and are sent along with the existing attachments.
To call the Generate Substitution file dialog, click
 on the Generate table’s toolbar. Use this dialog to define how ReadyAPI should generate attachments.
on the Generate table’s toolbar. Use this dialog to define how ReadyAPI should generate attachments.Option Description Size The size of the file to be generated. Content Type The MIME-type of the generated file. -
The Replace table allows you to define files to be used instead of the ones provided by the request. If you select to cache an attachment in the request, it will be stored in the project. Otherwise, the absolute path to the attachment is used instead.
-
Check the Remove option to send the request without the attachment. This overrides all other Generate and Replace settings.
Use the following options to configure the scan Strategy:
| Option | Description |
|---|---|
| Request Delay (ms) | Set a pause between requests during the scan in milliseconds. |
| Apply to Failed Test Steps | Select to run the scan even if the target test step fails. |
| Run only once | Select to run the scan only once for each test step, even if ReadyAPI runs that step several times for a test case. |
On the Advanced panel, specify the Request timeout(ms) to define time in milliseconds after which the request will be canceled.
Related materials
See Also
Sensitive Information Exposure Assertion
Response SLA Assertion
Security Scans Types