About
The Sensitive Files Exposure scan verifies that any files that cause security problems are not accessible through the service.
Typically, attackers try to use sensitive files for breaking the service or finding the information that may be useful for other types of attacks. The Sensitive Files Exposure scan searches for such files and notifies you if they exist.
If the scan does not reveal any information about possible vulnerabilities, it passes successfully.
If the scan has Failed, that means your service leaves sensitive files unprotected.
Requirements
-
This scan is applicable to REST test steps or REST requests.
-
To use this scan, you need a ReadyAPI Test
 license. If you do not have it, request it on our web site or start a trial.
license. If you do not have it, request it on our web site or start a trial.
How it works
The Sensitive Files Exposure scan processes a list of sensitive files and checks if any calls to these files receive an HTTP 200 response.
It uses assertions to validate each response and check if it includes any information about potential vulnerabilities.
If a response passes all assertions, PASS will be logged for that response. If any assertion fails, FAIL will be logged.
 |
If you have not applied any assertions to the scan, Unknown will be logged for the response. |
Assertions
-
Default Assertion
Sensitive File Exposure – Verifies that internal server files are not exposed (for example, by stack traces if the server crashes).
Parameters
The Sensitive Files Exposure Scan uses a list of sensitive files.
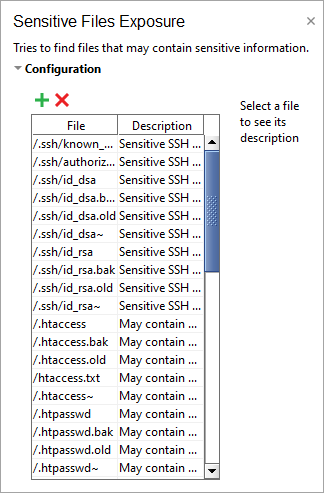
Add, remove, or edit items of the list as you need.
Use the following options to configure the scan Strategy:
| Option | Description |
|---|---|
| Request Delay (ms) | Set a pause between requests during the scan in milliseconds. |
| Apply to Failed Test Steps | Select to run the scan even if the target test step fails. |
| Run only once | Select to run the scan only once for each test step, even if ReadyAPI runs that step several times for a test case. |
